Monitoring Windows Event Logs
Windows event logs are essential for security, troubleshooting, and compliance. When you analyze your logs, you can monitor and report on file access, network connections, unauthorized activity, error messages, and unusual network and system behavior.
However, Windows servers produce tens of thousands of log entries every day. The sheer volume of data is almost impossible to go through manually—and most of these entries will show successful, problem-free interactions and transactions.
What Types of Events Are Logged By Windows and Can Be Viewed Using The Event Viewer?
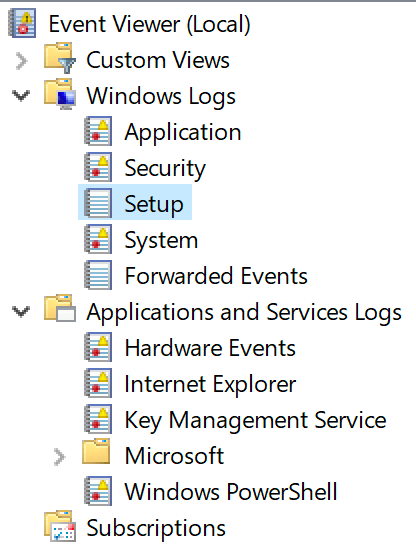
For Windows systems, there are three default types of event logs:
- System
- Application
- Security
Beyond the initial three categories, there are typically additional Windows Event Log channels, as seen in this screenshot from a Windows 10 system.
Getting into the Details on Windows Events
The cool thing about Windows Event Logs is that it is a treasure trove of data that can detect issues with the Windows environment and indicate potential problems. You need to know what to look for. Windows Event Logs give a blueprint of current conditions for the Windows systems. Applications and the built-in Windows Services use these event logs to record necessary hardware and software actions that the administrator can use to troubleshoot issues. The Windows operating system tracks specific events in its log files, such as application installations, system logins, network resource access, or errors.
Anatomy of a Windows Event
Here are some examples of data typically available via Windows Event Logs.
How Do I View Windows Events?
Windows Events can be viewed in Windows Event Viewer, which is built into every Windows installation (except for Windows Server Core). While Event Viewer helps view the local logs, it can connect to other Windows systems across your domain.
Generally, it is a good tool for troubleshooting single issues, but it could be better for looking at events across your environment.
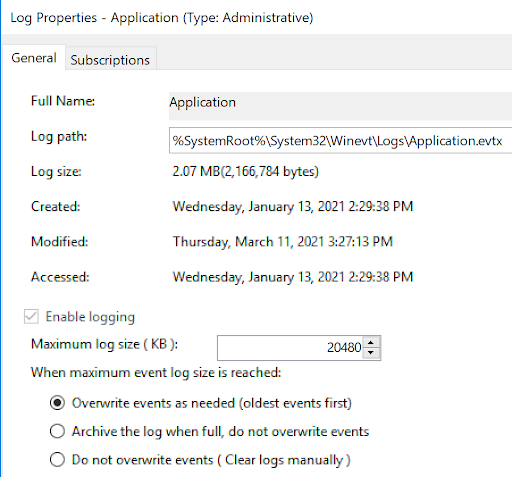
Should I Disable Windows Event Log?
No, the Windows Event Log is set to overwrite old entries at a maximum of 16 MB for each category. You don’t have to worry about the event’s data filling up too much storage.
This is configurable via the properties in the Event Viewer for the individual log.
Windows Event Logs in observIQ – What Is Collected
In observIQ, you can add a Source to a deployed agent that will collect logs from the machine the agent is deployed on. Configuration information collected includes the following, as represented in the table below:
Configuration
Setting Up Log Collection for Windows Event Logs
Assuming you already have an observIQ Log Agent deployed on a Windows machine (and we’d be remiss not to mention our log agent, Stanza, is the official log agent of the OpenTelemetry project), the first step will be to add the Windows Event Log source to the agent you want to use to collect Windows Event Logs with.
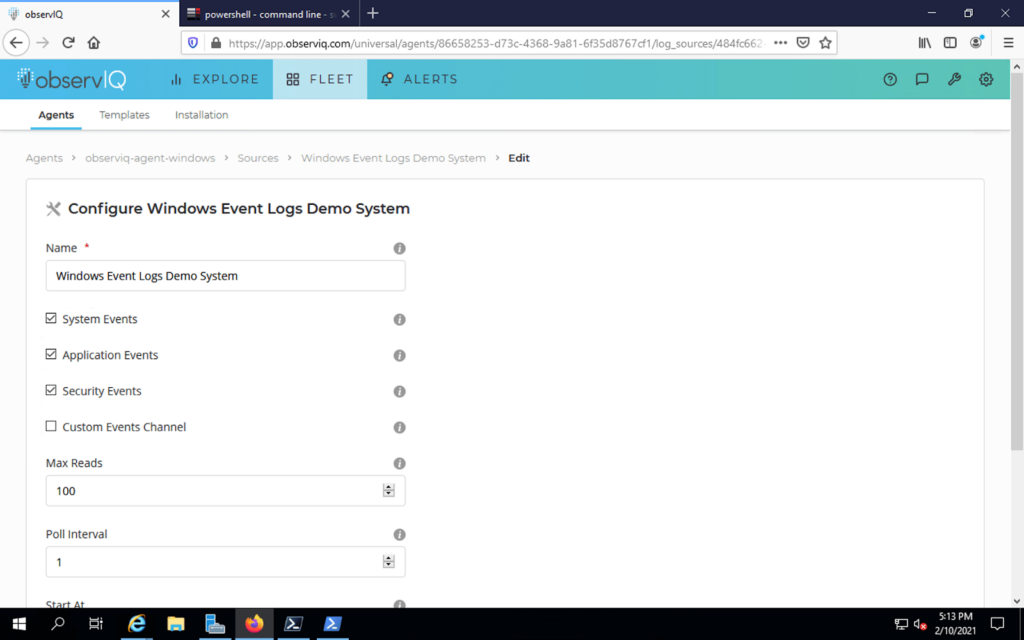
You are allowed to collect system, application, and security logs. You can also define your list of additional Event channels. If you have questions about which category of logs you wish to collect, each option includes a summary description of the logs collected. You can elect to collect all categories of logs as well.
The source configuration dialogue box provides an advanced invocation option if you want to collect logs in a custom format and potentially attach custom metadata.
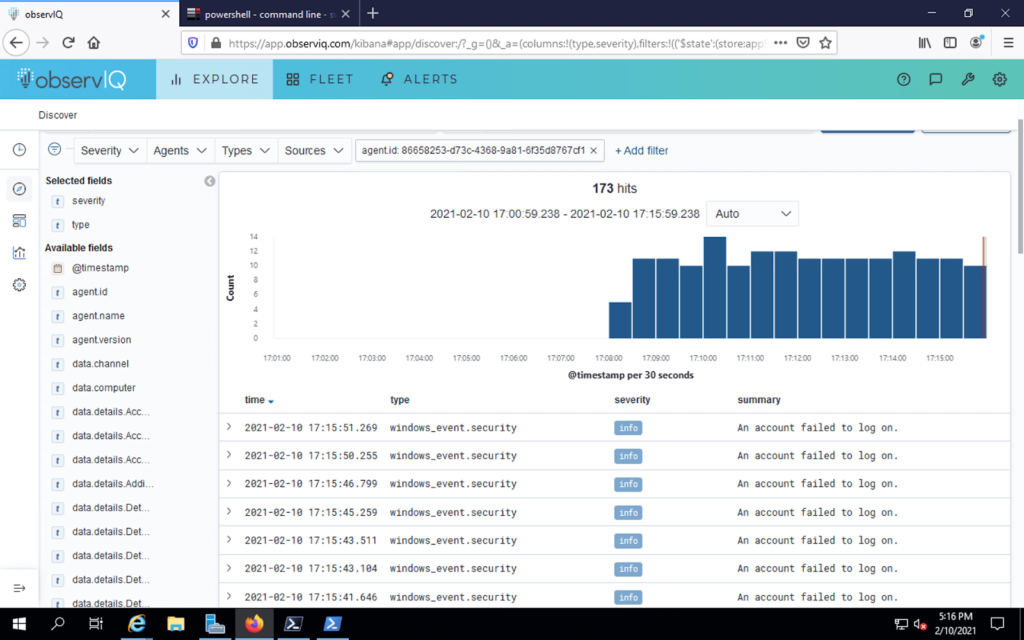
Once configured, logs flow in the Kibana log visualization element of observIQ Cloud.
Happy Logging!