Integrating BindPlane Into Your Splunk Environment (Part 2)
Part 2 of 3: Other Sources & Destinations
Preface
It can often be challenging to collect data into a monitoring environment that does not natively support that data source. Bindplane can help solve this problem. As the Bindplane Agent is based on OpenTelemetry (and is also as freeform as possible), one can bring in data from disparate sources that the Splunk Universal Forwarder does not easily support.
Prerequisites
- The environment built in Part 1
- Additional data sources
- For the blog, I will be using /var/log/messages as an additional data source.
- This source could be added to the Splunk UF, but it is easier to collect it directly.
- Logs in /var/log often require creating custom source types or downloading community Apps/TA.
New Source In BindPlane
In Bindplane, we want to add a new source to our configuration. This will be a File source. The following configuration values need to be set:
- File(s): /var/log/messages
- Log Type: var_log_messages (This is optional)
- Parse Format: regex
- Regex Pattern: (?P<timestamp>\w{3}\s\d{2}\s\d{2}:\d{2}:\d{2})\s(?P<hostname>[^\s]+)\s(?P<process_name>[^\[]+)\[(?P<pid>\d+)\]:\s(?P<message>.+)
- Parse Timestamp Checkbox: Checked
- Timestamp Field: timestamp
- Timestamp Format: Manual
- Timestamp Layout: %b %e %T
- 3-letter month abbreviation (%b)
- Space padded day of month (%e)
- HH:MM:SS (%T)
- Timezone set to the tz of the server; for me this is: America/Detroit
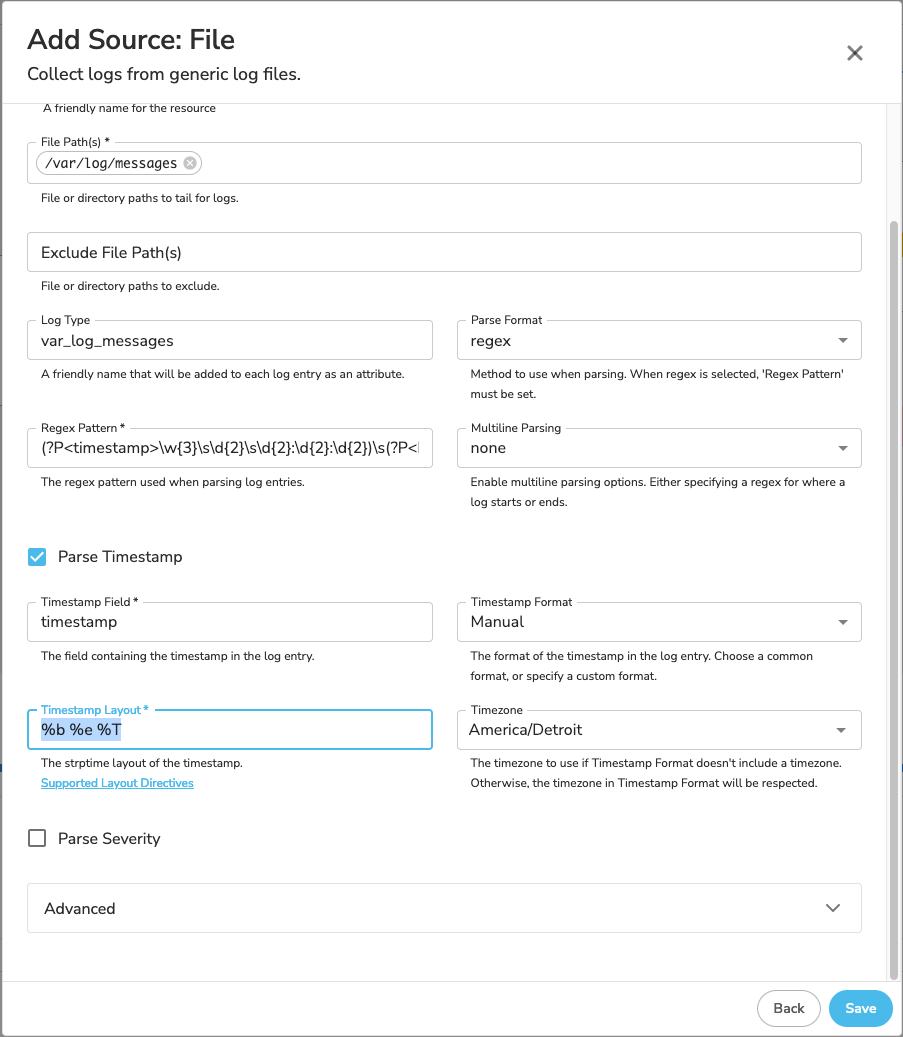
Save this new source, and click “Start Rollout” to apply it to the agent(s)
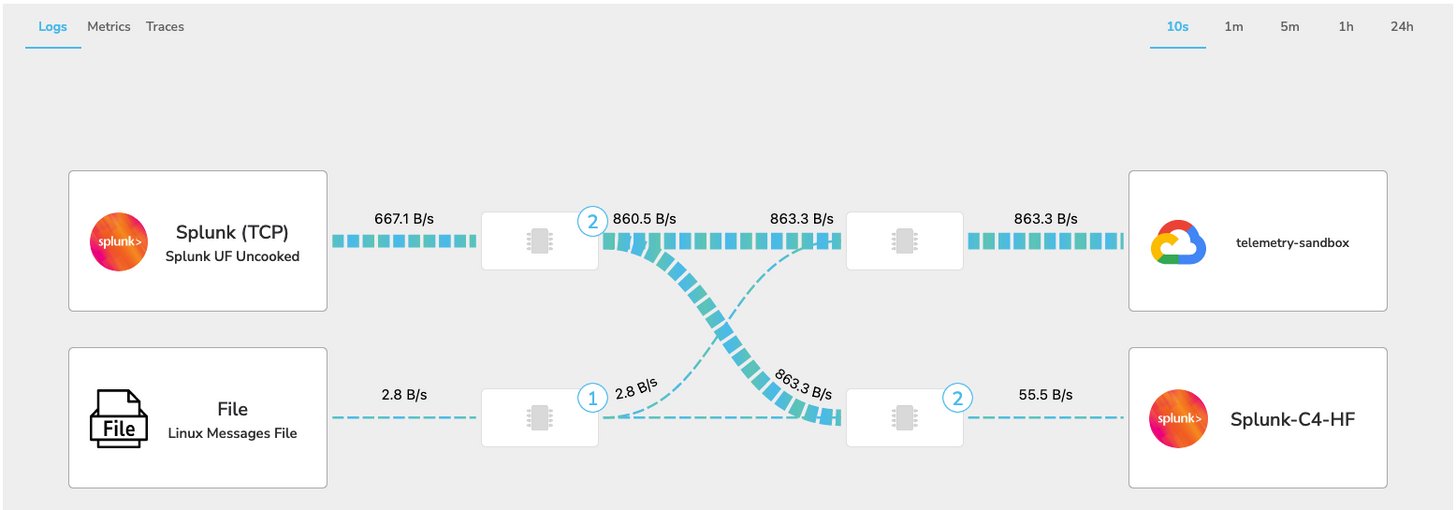
Data Flowing
We can see our updated topology view’s data flow diagram with the new source in.
For consistency with the Splunk source metadata, I added a processor to add a new body field called `entry_type` set to `LinuxSystemMessages.` I extract this field on the Splunk side for easy searches.
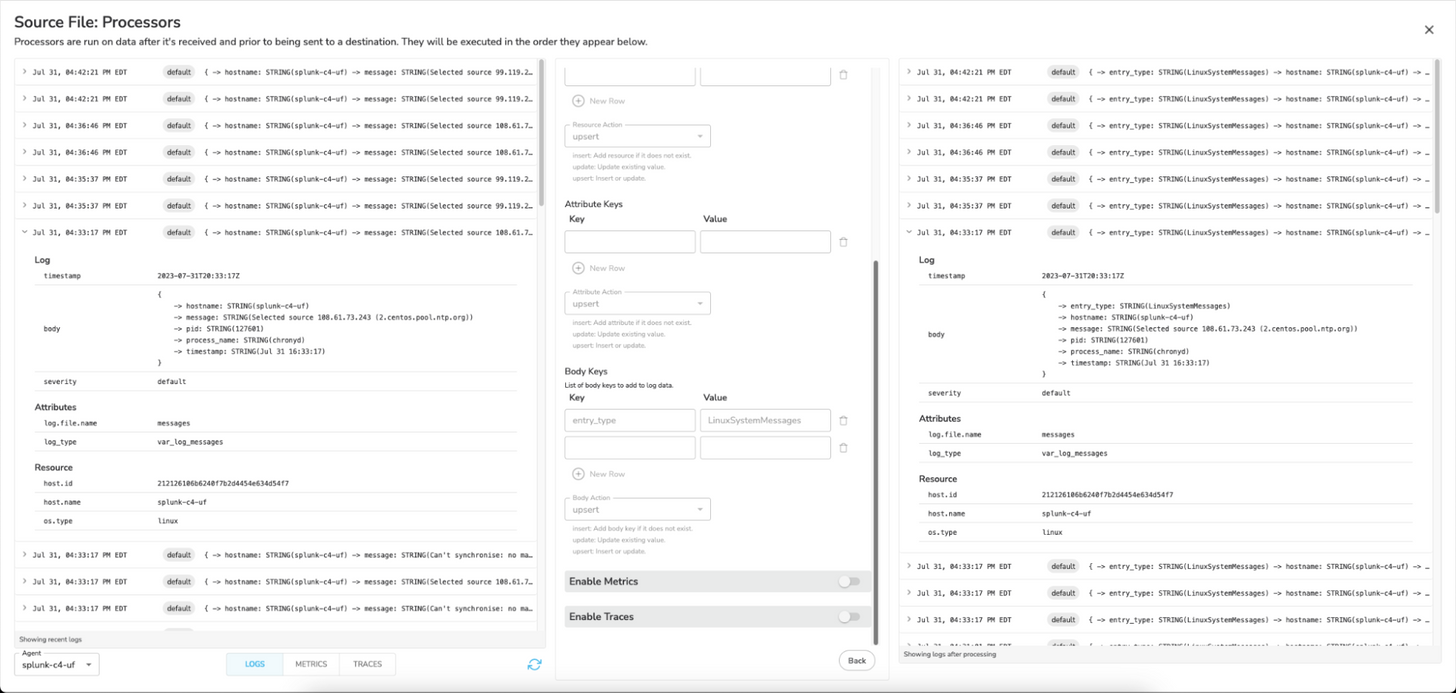
In Splunk, this will look like so:
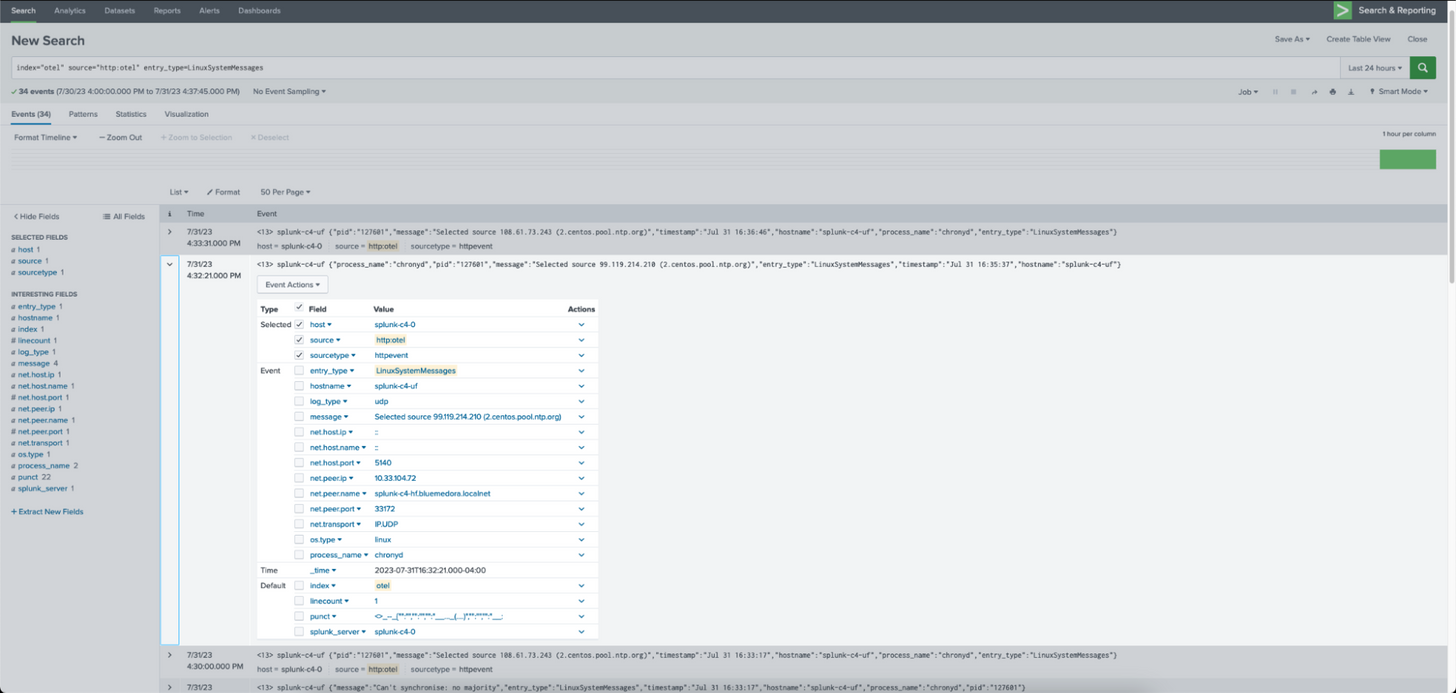
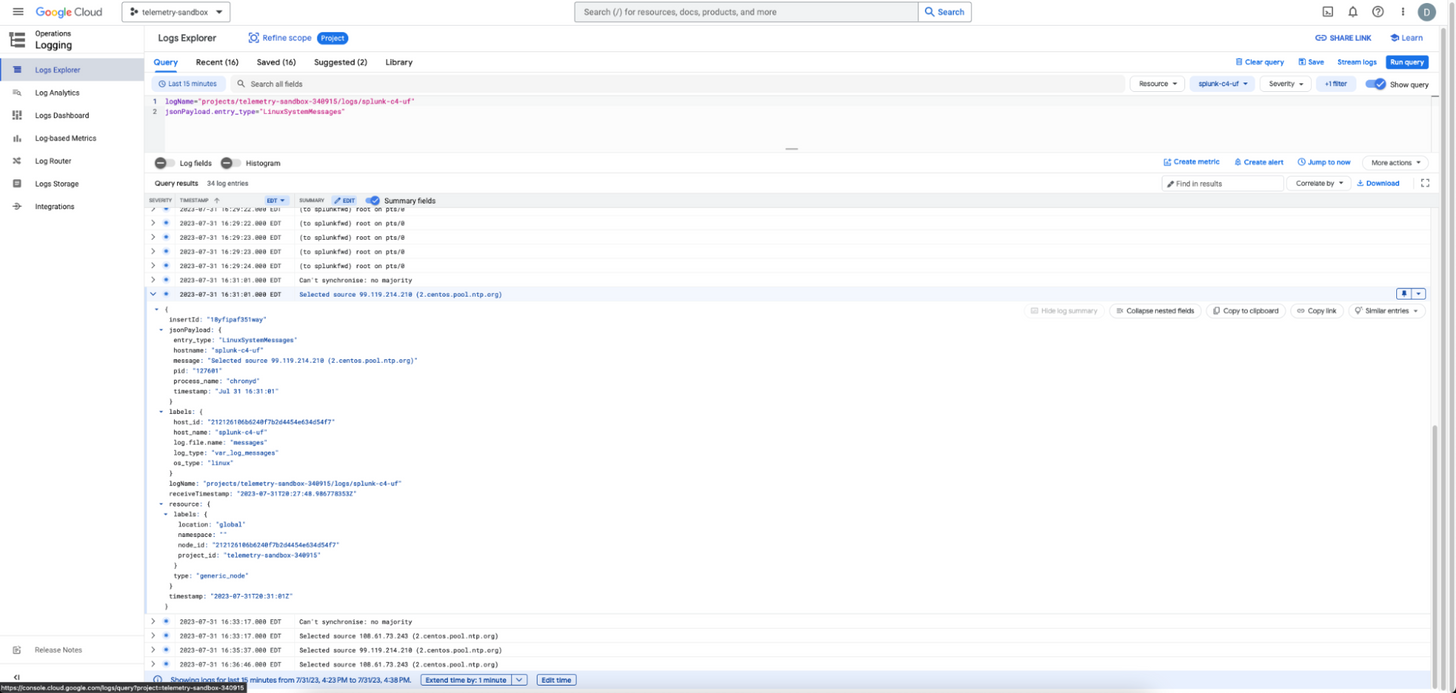
The same search in Google Cloud Logging will look like this:
Conclusion
Using a Bindplane Agent to collect log data, virtually any logs can be sent to Splunk. Sending these logs to Google Cloud Logging or any other supported platform can also satisfy different use cases. It can also be used when moving from Splunk to another platform or vice versa. Allowing you to, for a time, send data to both platforms. This aids transition by overlapping the two platforms and allowing you to make sure the new platform’s capabilities match or exceed the ones you are leaving. Breaking vendor lock is one of the topics we will examine in part 3 as we continue to build on our environment.
Follow this space to keep up with all our future posts and simplified configurations for various sources. For questions, requests, and suggestions, contact our support team at support@observIQ.com or join our community Slack Channel.



